Custom alerts and data visualization let you quickly identify cybersecurity threats and prevent security incidents.
As part of your central security plan and security compliance, Paessler PRTG is your reliable addition to standalone network security tools. Our comprehensive network monitoring software adds a double layer of protection by working in real time to quickly identify irregularities and threats and keeping your network secure.
No need to juggle several different monitoring tools at once. The central dashboard of PRTG provides the overview you need – at one glance only.
Keep a constant eye not only on security-relevant network data and devices, but also on other services and processes in your entire IT environment.
Make sure that the hardware and software that’s important for your network’s security is available and functioning round the clock.
PRTG monitors all your network devices and applications 24/7, including firewalls, ports, routers, switches, VPN connections, antivirus software, and more.
The built-in alarm feature of PRTG is fully customizable. Choose your own warning and error threshold values and how you’d like to be informed.
As soon as PRTG detects suspicious activity or unusual traffic patterns on your network, it alerts you via SMS, email, in-app push notification, and other methods.
Every PRTG sensor is equipped with an “unusual” sensor status, and will automatically sound the alarm if values emerge which are inconsistent with previous ones.
Such values may be indicative of security problems – comparing and analyzing them with PRTG’s historical data will help you troubleshoot potential threats and vulnerabilities more efficiently.
Diagnose network issues by continuously tracking the availability and performance of security-relevant hardware and software. Show update status, unusual activities, network traffic flows, bottlenecks, unauthorized access, and other key metrics for threat detection in real time. Visualize monitoring data in clear graphs and dashboards to identify problems more easily. Gain the overview you need to troubleshoot all kinds of cybersecurity issues in your network.
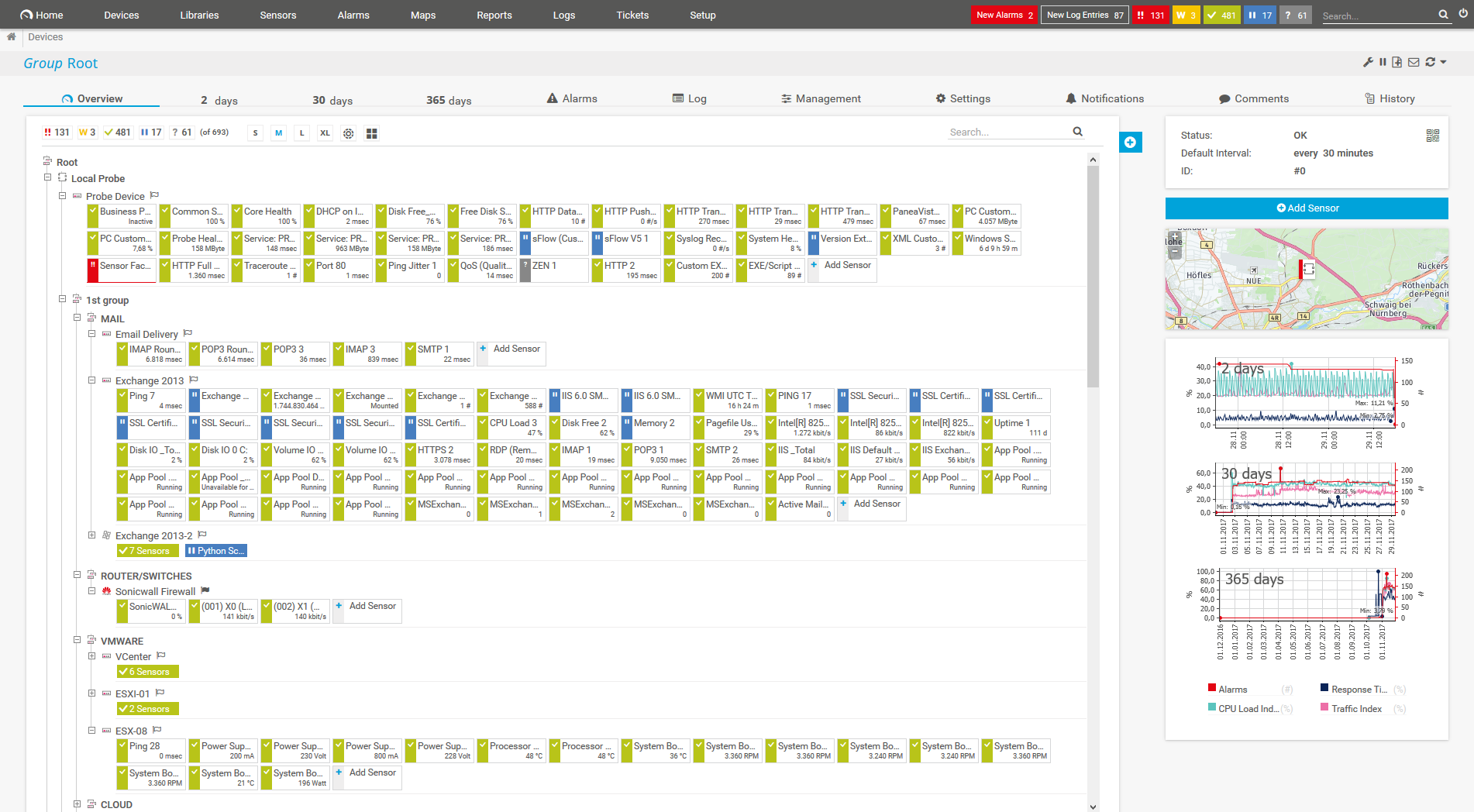
Device tree view of the complete monitoring setup

Custom PRTG dashboard for keeping an eye on the entire IT infrastructure
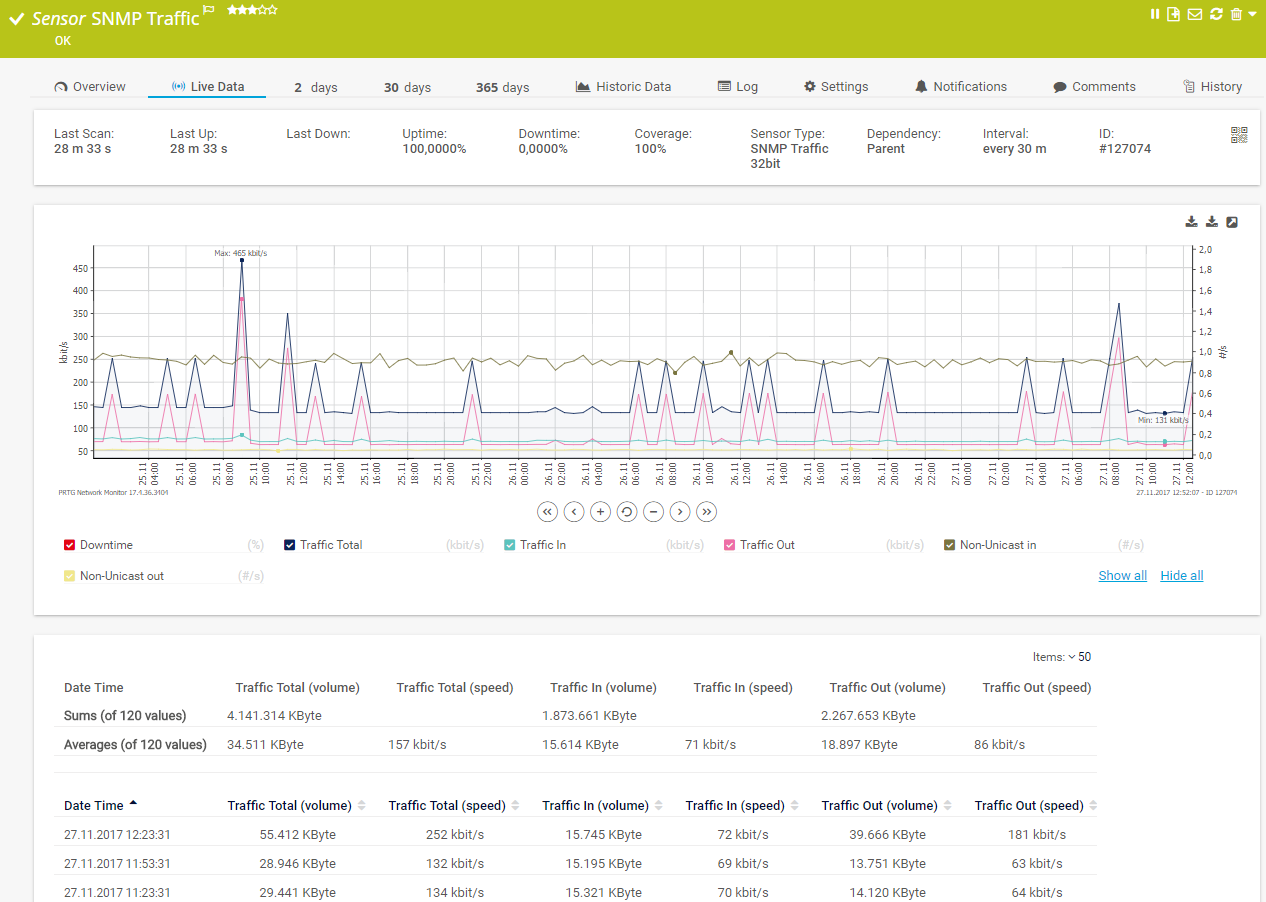
Live traffic data graph in PRTG
PRTG comes with more than 250 native sensor types for monitoring your entire on-premises, cloud, and hybrid cloud environment out of the box. Check out some examples below!
See the PRTG Manual for a list of all available sensor types.
Custom alerts and data visualization let you quickly identify cybersecurity threats and prevent security incidents.
PRTG is set up in a matter of minutes and can be used on a wide variety of mobile devices.
“Excellent tool for detailed monitoring. Alarms and notifications work greatly. Equipment addition is straight forward and server initial setup is very easy. ...feel safe to purchase it if you intend to monitor a large networking landscape.”
Partnering with innovative IT vendors, Paessler unleashes synergies to create
new and additional benefits for joined customers.
Axis offers one of the most complete and reliable product portfolios, an expanded professional network, and comprehensive integration support for video management software.
Combining PRTG’s broad monitoring feature set with IP Fabric’s automated network assurance creates a new level of network visibility and reliability.
With ScriptRunner Paessler integrates a powerful event automation platform into PRTG Network Monitor.
Real-time notifications mean faster troubleshooting so that you can act before more serious issues occur.
Network Monitoring Software – Version 25.3.110.1313 (August 27, 2025)
Download for Windows and cloud-based version PRTG Hosted Monitor available
English, German, Spanish, French, Portuguese, Dutch, Russian, Japanese, and Simplified Chinese
Network devices, bandwidth, servers, applications, virtual environments, remote systems, IoT, and more
Choose the PRTG Network Monitor subscription that's best for you
Network security refers to the practices, policies, and technologies used to protect the integrity, confidentiality, and availability of a network and its data from unauthorized access, misuse, or harm. It encompasses a wide range of measures designed to protect both the hardware and software components of a network, as well as the data being transmitted across it.
Network security is crucial for protecting sensitive data, maintaining the trust of customers and users, and ensuring the continuous operation of business and personal networks. As cyber threats continue to evolve, robust network security measures are essential for defending against increasingly sophisticated attacks.
Common network security measures include:
Network security monitoring (NSM) involves the continuous observation of a network to detect and respond to potential security threats, vulnerabilities, and anomalous behavior in real-time. It is a critical component of a broader security strategy that helps organizations protect their networks from attacks and unauthorized access.
Key components of network security monitoring tools (NSM tools) like Paessler PRTG include:
In PRTG, “sensors” are the basic monitoring elements. One sensor usually monitors one measured value in your network, for example the traffic of a switch port, the CPU load of a server, or the free space on a disk drive. On average, you need about 5-10 sensors per device or one sensor per switch port.
Paessler conducted trials in over 600 IT departments worldwide to tune its network monitoring software closer to the needs of sysadmins. The result of the survey: over 95% of the participants would recommend PRTG – or already have.
Paessler PRTG is used by companies of all sizes. Sysadmins love PRTG because it makes their job a whole lot easier.
Bandwidth, servers, virtual environments, websites, VoIP services – PRTG keeps an eye on your entire network.
Everyone has different monitoring needs. That’s why we let you try PRTG for free.