Custom alerts and data visualization make it easy to monitor, identify, and prevent network security issues.
Security issues on your network can have disastrous consequences not only for your IT infrastructure, but for your entire business. Even the best firewalls are no guarantee of total IT protection.
Misconfigurations, unnecessarily open ports, and malware not only compromise the internal network, but also present a serious threat to overall IT security.
A vulnerability assessment, or a penetration test (pentest), can identify potential security gaps in applications or apps, operating systems like Windows and Linux, and hardware such as switches and routers. It does not matter whether the systems are on-premises or in the cloud.
Our all-one-one network monitoring tool Paessler PRTG helps you to uncover and eliminate security vulnerabilities in your IT infrastructure!
Diagnose network issues by continuously monitoring the security of your infrastructure. Show suspicious network traffic, unauthorized access, missing patches, and more in real time and visualize data in graphic maps & dashboards to identify problems more easily. Gain the network visibility you need to troubleshoot potential network vulnerabilities.
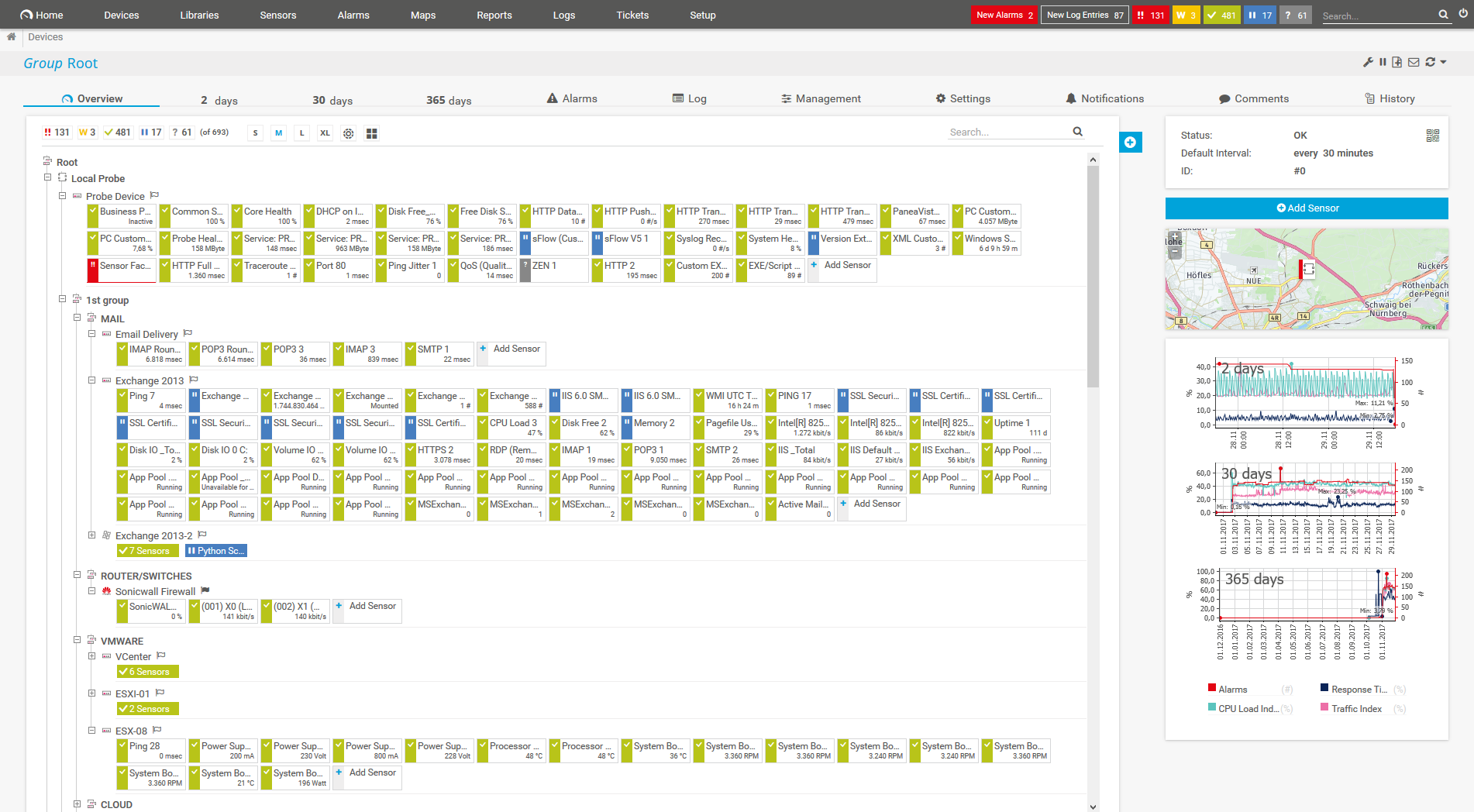
Device tree view of the complete monitoring setup
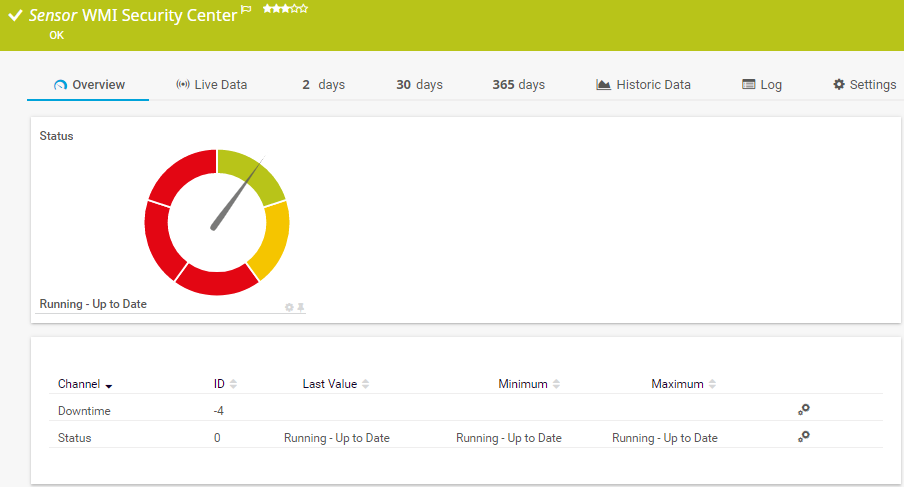
Preconfigured WMI Security Center sensor in PRTG

Custom PRTG dashboard for keeping an eye on the entire IT infrastructure
Stay informed about your network with advanced alerting options. PRTG notifies you in real time as soon as it detects potential security issues – for immediate security assessment and remediation.
Generate automated reports with PRTG to gain insight into your network’s security status and identify areas that need attention or improvement.
Keep an eye on your bandwidth usage to detect unusual traffic spikes that could signal a security threat or malware activity.
Use PRTG to analyze traffic patterns and detect unauthorized access attempts that indicate vulnerabilities or ongoing hacker attacks.
Track open ports on network devices and detect unnecessary open ports that pose security risks, allowing you to close them and reduce the attack surface.
Collect detailed information from network endpoints, switches, routers and servers. This information helps you identify misconfigurations or outdated firmware that could be exploited.
Create custom sensors or use templates in PRTG to define specific checks for security-relevant configurations and ensure compliance with your security policies.
By monitoring logs from different devices and applications, you can identify security events such as failed logon attempts, suspicious activity, and configuration changes.
PRTG comes with more than 250 native sensor types for monitoring your entire on-premises, cloud, and hybrid cloud environment out of the box. Check out some examples below!
See the PRTG Manual for a list of all available sensor types.
Real-time alerts and custom notifications make it easy to solve issues with unauthorized access, open ports, and other potential security loopholes.
Paessler PRTG alerts you when new or unauthorized devices connect to the network. This helps you to take immediate action and prevent potential security breaches.
Monitor the update status of applications and hardware. PRTG highlights devices with outdated firmware that may contain security vulnerabilities and helps you update them in time.
Monitor the status and configuration of your firewalls to ensure they are up and running and securely configured to protect the network perimeter.
Custom alerts and data visualization make it easy to monitor, identify, and prevent network security issues.
PRTG is set up in a matter of minutes and can be used on a wide variety of mobile devices.
Partnering with innovative IT vendors, Paessler unleashes synergies to create
new and additional benefits for joined customers.
Monitor all major physical hazards in IT rooms and racks such as critical climate factors, fire or burglary.
Asset visibility is a big problem for many IT teams. Not having an accurate inventory of tech assets is inefficient, costly and a potential security risk.
Osirium’s experienced management team has an outstanding track record in cybersecurity and automation, establishing its headquarters near Reading, UK.
Real-time alerts and custom notifications make it easy to solve issues with unauthorized access, open ports, and other potential security loopholes.
Network Monitoring Software – Version 25.3.110.1313 (August 27, 2025)
Download for Windows and cloud-based version PRTG Hosted Monitor available
English, German, Spanish, French, Portuguese, Dutch, Russian, Japanese, and Simplified Chinese
Network devices, bandwidth, servers, applications, virtual environments, remote systems, IoT, and more
Choose the PRTG Network Monitor subscription that's best for you
Network vulnerability scanning or vulnerability detection automatically scans networks for security gaps and vulnerabilities. It uses databases of known vulnerabilities to identify potential risks and generates reports with recommendations for solving these issues. The scanner inventories network devices, checks configurations, and prioritizes vulnerabilities based on risk. It can run periodic vulnerability tests and integrate with other security tools to ensure continuous network security.
PRTG as a network vulnerability scanner scans all devices and applications in your network at defined intervals and notifies you of potential risks that may exist.
Good network vulnerability scanning tools should possess a range of features to effectively identify, analyze, and manage security vulnerabilities in a network. Here are some of the key features to look for:
1. Comprehensive scanning:
2. Accuracy:
3. Customization and flexibility:
4. User-friendly interface:
5. Integration capabilities:
6. Real-time monitoring and alerts:
Intrusion detection is the monitoring and analysis of computer systems or network activity to identify unauthorized access or security breaches. Techniques include network-based and host-based monitoring, as well as signature and anomaly detection methods. One challenge in intrusion detection is managing false positives, which are false alarms that indicate a potential threat that is not actually present.
PRTG helps you with intrusion detection by monitoring network traffic and cloud-based web applications, and using an analyzer to detect suspicious unusual activity or potential cyberattacks in real time.
Vulnerability management is the systematic process of identifying, assessing, and troubleshooting security vulnerabilities in systems and networks. It involves scanning for vulnerabilities, prioritizing them based on severity and impact (such as CVEs - Common Vulnerabilities and Exposures), and solving them with patches or security controls.
PRTG tracks the status of security patches and updates on network devices and servers, and identifies new devices connected to the network.
Access control monitoring oversees and regulates who can access specific resources, data, or areas within a system or organization. It continuously monitors user activity, permissions, and authentication processes to ensure compliance with security policies and detect unauthorized access attempts. In addition, cybersecurity and automation play a critical role in enhancing these monitoring processes, streamlining response actions, and reducing the risk of human error.
PRTG monitors user access to critical systems and resources and detects unauthorized access attempts.
Asset management is the process of identifying, inventorying, and controlling all devices that have access to an organization's network and resources. This includes maintaining a comprehensive inventory, implementing access controls, and monitoring device activity for compliance with security policies.
PRTG helps you with your asset management by keeping track of all network devices and their configurations to ensure that only authorized devices are connected to the network.
Compliance monitoring is the ongoing process of tracking, assessing, and ensuring conformance to regulatory requirements, industry standards, internal policies, and best practices. It systematically monitors activities, processes, and controls to verify alignment with compliance frameworks and policies.
PRTG monitors network activities to ensure compliance with industry regulations and standards such as GDPR, HIPAA, PCI DSS, etc.
In PRTG, “sensors” are the basic monitoring elements. One sensor usually monitors one measured value in your network, for example the traffic of a switch port, the CPU load of a server, or the free space on a disk drive. On average, you need about 5-10 sensors per device or one sensor per switch port.
Paessler conducted trials in over 600 IT departments worldwide to tune its network monitoring software closer to the needs of sysadmins. The result of the survey: over 95% of the participants would recommend PRTG – or already have.
Paessler PRTG is used by companies of all sizes. Sysadmins love PRTG because it makes their job a whole lot easier.
Bandwidth, servers, virtual environments, websites, VoIP services – PRTG keeps an eye on your entire network.
Everyone has different monitoring needs. That’s why we let you try PRTG for free.