Custom alerts and data visualization let you quickly identify and prevent OT security issues.
It’s no longer recommended to isolate OT environments from the outside world as a security strategy. IT/OT convergence, the digitalization of OT networks, the need to give equipment vendors remote access, and the need to collect, analyze, and store sensor data from IIoT applications all require industrial networks to be connected to external systems or devices.
And that means: They are vulnerable to attack.
That is why monitoring forms a crucial part of any Operation Technology (OT) cybersecurity strategy. Paessler PRTG monitoring software can help make your industrial IT infrastructure more secure.
There are various strategies for keeping OT networks safe and secure, and PRTG can play an important role in each.
Diagnose network issues by continuously tracking your IT, OT, and IIoT networks. cybersecurity risks such as hacker, malware, and ransomware attacks in real time. Visualize monitoring data in clear graphs and dashboards to identify problems more easily. Gain the overview you need to troubleshoot disruptions in production and business processes, as well as supply chains.
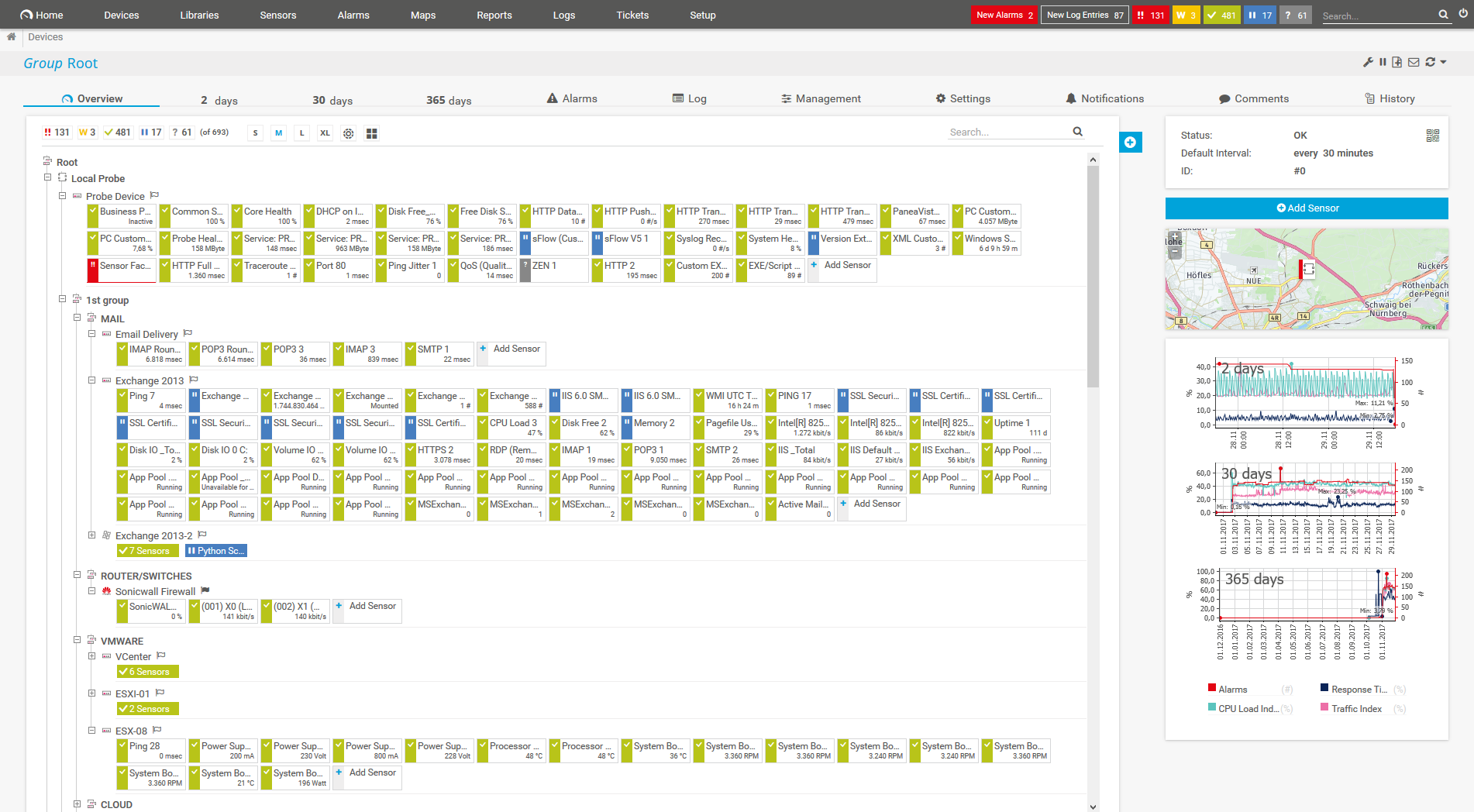
Device tree view of the complete monitoring setup
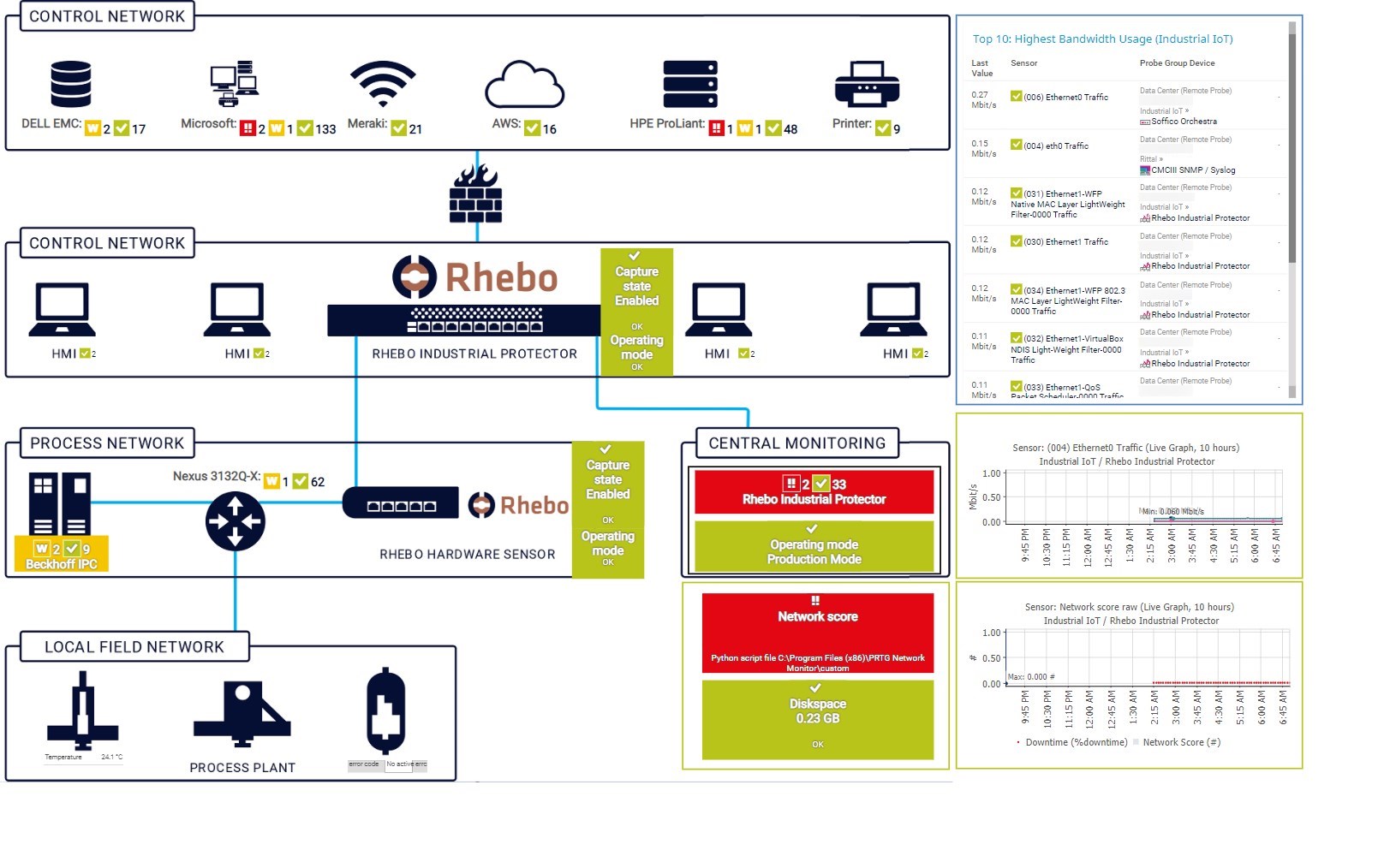
Custom PRTG dashboard for Rhebo uptime alliance
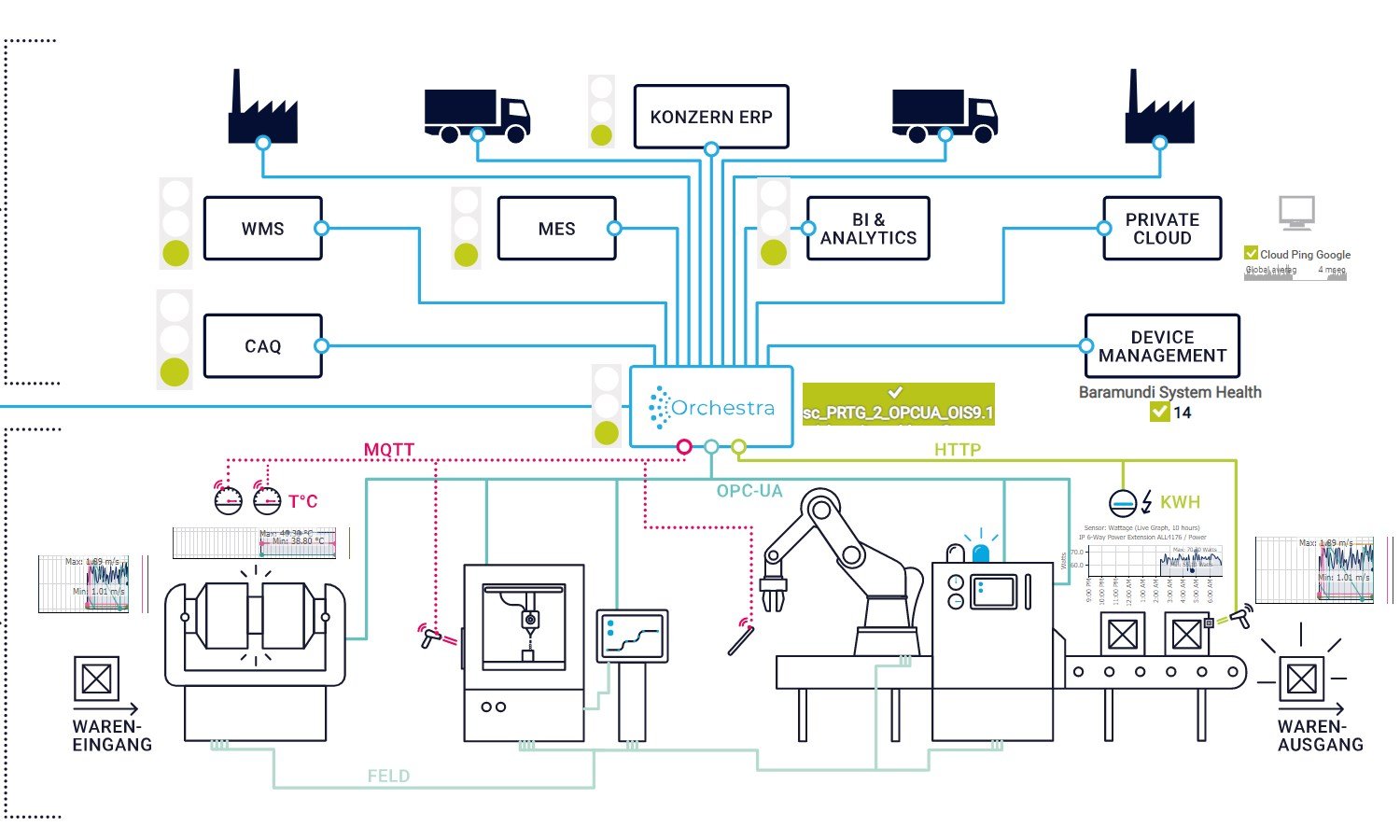
Custom PRTG map for Orchestra
OT security practices are not only about cybersecurity detection and mitigation. It’s about the physical security of your factory buildings and production lines, too. PRTG helps you in various ways to prevent unauthorized access and hazards such as fire and water damage.
IP camera systems consist of multiple components: surveillance cameras, video recorders, power supplies, and network and data transmission systems.
PRTG helps you watch the watchers by continuously monitoring the availability, health, and performance of your entire CCTV system.
IoT sensors are commonly used to monitor environmental conditions on the factory floor, such as temperature, humidity, vibration levels, voltage and more, as well as access to doors or windows.
Using SNMP, MQTT, and other technologies, PRTG retrieves data from IoT devices and alerts you as soon as there is an issue.
Real-time notifications mean faster troubleshooting so that you can act before more serious issues occur.
PRTG is monitoring software that can keep an eye on the health, status, and condition of all kinds of components across IT, OT, and IIoT:
Custom alerts and data visualization let you quickly identify and prevent OT security issues.
PRTG is set up in a matter of minutes and can be used on a wide variety of mobile devices.
“Excellent tool for detailed monitoring. Alarms and notifications work greatly. Equipment addition is straight forward and server initial setup is very easy. ...feel safe to purchase it if you intend to monitor a large networking landscape.”
Partnering with innovative IT vendors, Paessler unleashes synergies to create
new and additional benefits for joined customers.
By integrating PRTG with Martello iQ, you can add a fast analytics layer to improve uptime, visualize your IT environment, and integrate all of your IT systems into a single pane of glass.
With the combination of PRTG and Insys, the monitoring specialist Paessler and the industrial gateway manufacturer INSYS icom offer a practical possibility to merge IT and OT.
With condition monitoring and retrofitting, PRTG and Schildknecht DATAEAGLE make even older production plants competitive.
Real-time notifications mean faster troubleshooting so that you can act before more serious issues occur.
Network Monitoring Software – Version 25.3.110.1313 (August 27, 2025)
Download for Windows and cloud-based version PRTG Hosted Monitor available
English, German, Spanish, French, Portuguese, Dutch, Russian, Japanese, and Simplified Chinese
Network devices, bandwidth, servers, applications, virtual environments, remote systems, IoT, and more
Choose the PRTG Network Monitor subscription that's best for you
Operational Technology (OT) cybersecurity refers to the protection of systems and networks that control and monitor physical processes in industries such as manufacturing, energy, transportation, and utilities. These systems include industrial control systems (ICS), supervisory control and data acquisition (SCADA) systems, distributed control systems (DCS), and other specialized hardware and software that are used to operate industrial processes.
A robust OT cybersecurity strategy is essential for several reasons, all of which contribute to the overall security, reliability, and efficiency of critical infrastructure and industrial operations. Here are the main reasons why having a strong OT cybersecurity strategy is a good idea:
Developing an effective cybersecurity strategy for OT environments requires a comprehensive approach that addresses the unique challenges and requirements of OT devices and systems.
Here are some aspects that should be considered:
In PRTG, “sensors” are the basic monitoring elements. One sensor usually monitors one measured value in your network, for example the traffic of a switch port, the CPU load of a server, or the free space on a disk drive. On average, you need about 5-10 sensors per device or one sensor per switch port.
Paessler conducted trials in over 600 IT departments worldwide to tune its network monitoring software closer to the needs of sysadmins. The result of the survey: over 95% of the participants would recommend PRTG – or already have.
Paessler PRTG is used by companies of all sizes. Sysadmins love PRTG because it makes their job a whole lot easier.
Bandwidth, servers, virtual environments, websites, VoIP services – PRTG keeps an eye on your entire network.
Everyone has different monitoring needs. That’s why we let you try PRTG for free.