Custom alerts and data visualization let you quickly identify and prevent data leaks and other security threats.
Data breach prevention relies on multiple tools and strategies: firewalls, strong passwords, antivirus software, and intrusion detection systems are just some examples of concepts to combat data breaches through ransomware, supply chain and other network attacks, or account takeovers, for example. And sitting beside all of these is comprehensive infrastructure monitoring.
Unusual network traffic, such as sudden spikes or inexplicable bottlenecks, are a good indicator of suspicious activity in your network.
PRTG lets you leverage protocols like SNMP, flow, and others to monitor bandwidth usage in real-time and identify potential cyberattacks while they are occurring.
Data breach protection is only as good as the cybersecurity tools that provide it. So if your firewalls, antivirus software, or other security endpoints are down, your network is exposed.
With PRTG, you can constantly monitor your security measures and receive instant alerts if they are not functioning as they should.
Even with the best network security solutions and tools in place, there’s always the chance that hackers find their way in. If you’re the victim of an attack and want to investigate the damage, then historical monitoring data is key.
PRTG stores monitoring data over time and gives you the possibility to trace events and activities to improve your threat intelligence.
Diagnose network issues by continuously tracking the health and security of your network. Show the status of your security hardware and software and other key metrics in real time. Visualize monitoring data in clear graphs and dashboards to identify problems more easily. Gain the overview you need to troubleshoot potential network vulnerabilities.
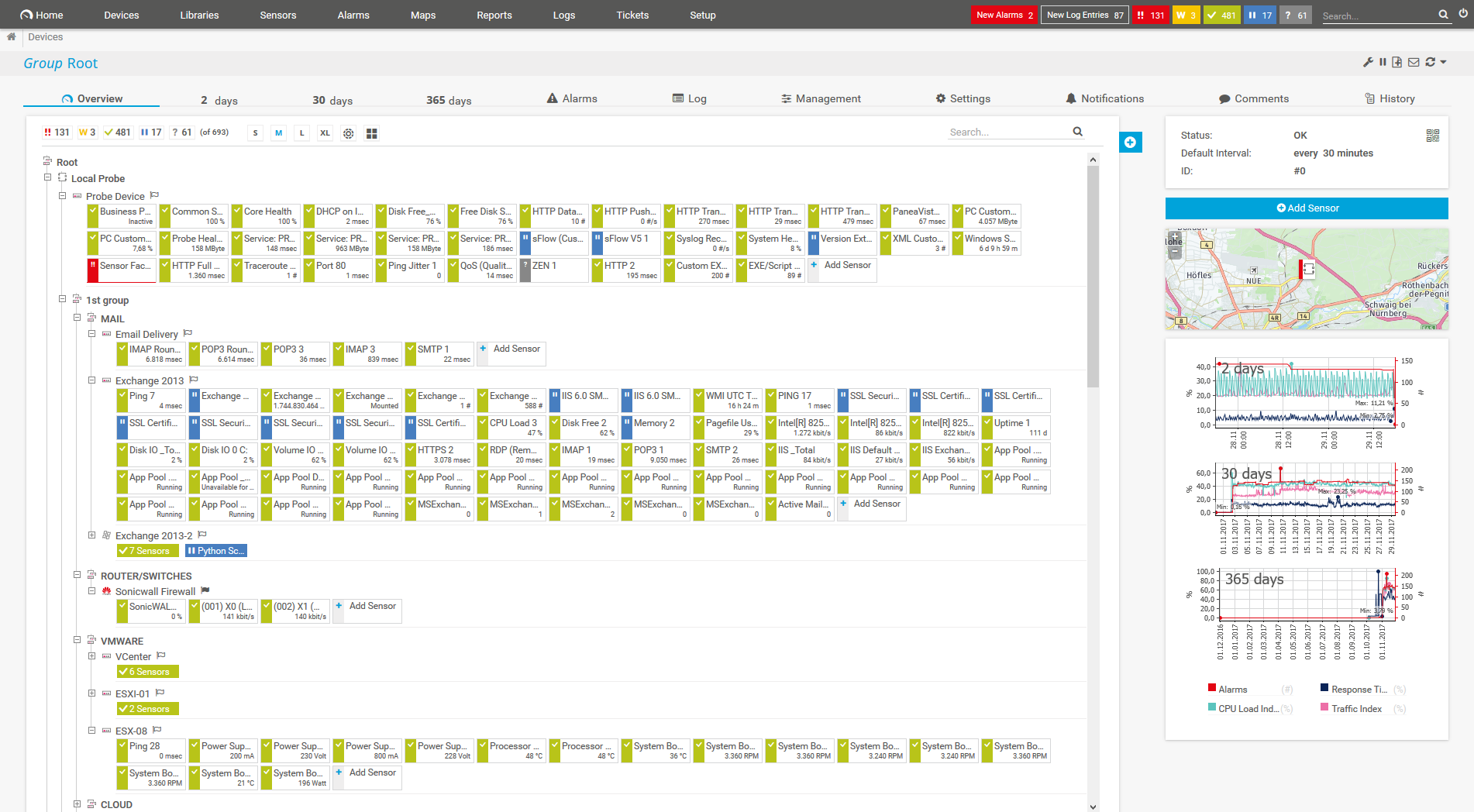
Device tree view of the complete monitoring setup
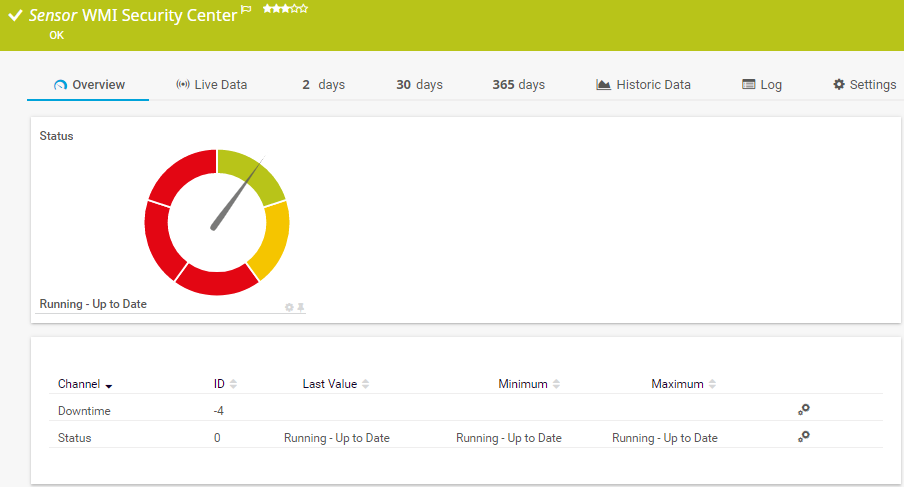
WMI Security Center Sensor overview
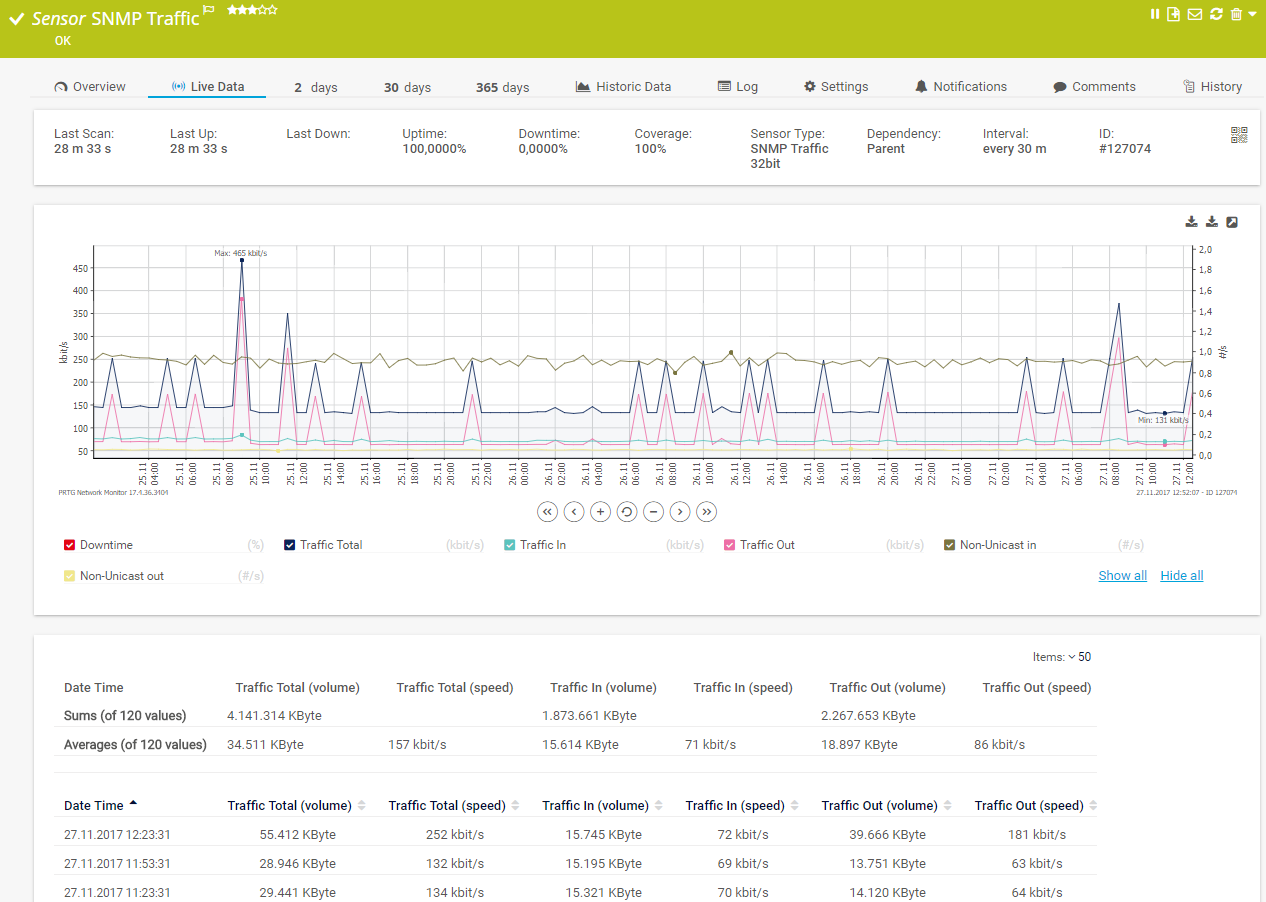
Live traffic data graph in PRTG
Configure PRTG to trigger alerts immediately based on individually defined thresholds when it detects anomalies that might indicate a cyber threat. Customizable notifications mean you can be alerted by push notifications, email, SMS, and many other ways.
Interactive dashboards and network maps in PRTG let you display cybersecurity information in different ways, so your teams can see the data they need quickly and easily. See the big picture or drill down to individual devices or systems – it’s up to you.
Preventing data breaches is more than just detecting suspicious activity. It means truly understanding your network and everything in it. Only this way can you know where possible vulnerabilities are. PRTG gives you an overview of everything with comprehensive network monitoring.
PRTG comes with more than 250 native sensor types for monitoring your entire on-premises, cloud, and hybrid cloud environment out of the box. Check out some examples below!
See the PRTG Manual for a list of all available sensor types.
Custom alerts and data visualization let you quickly identify and prevent security threats such as data leaks.
PRTG is set up in a matter of minutes and can be used on a wide variety of mobile devices.
Partnering with innovative IT vendors, Paessler unleashes synergies to create
new and additional benefits for joined customers.
Axis offers one of the most complete and reliable product portfolios, an expanded professional network, and comprehensive integration support for video management software.
Osirium’s experienced management team has an outstanding track record in cybersecurity and automation, establishing its headquarters near Reading, UK.
Rhebo and PRTG offer a comprehensive monitoring solution for IT and OT environments: from condition monitoring through to anomaly and threat detection.
Real-time notifications mean faster troubleshooting so that you can act before more serious issues occur.
Network Monitoring Software – Version 25.3.110.1313 (August 27, 2025)
Download for Windows and cloud-based version PRTG Hosted Monitor available
English, German, Spanish, French, Portuguese, Dutch, Russian, Japanese, and Simplified Chinese
Network devices, bandwidth, servers, applications, virtual environments, remote systems, IoT, and more
Choose the PRTG Network Monitor subscription that's best for you
A data breach is a security incident where cybercriminals and hackers gain access to confidential or sensitive data, such as credit card details, personal identity details, and more. Data breaches can be caused by cyberattacks or malware, for example. The compromised data can then be misused for fraudulent activities, identity theft, or sold on the dark web, potentially causing harm to individuals and organizations.
Data breaches can be prevented by implementing a comprehensive cybersecurity strategy that includes multiple layers of protection. This includes strong encryption for sensitive data, regular software updates, patch management, strict control of data security, employee training on cybersecurity best practices, and regular security audits and penetration testing.
In addition, software solutions such as intrusion detection systems and infrastructure monitoring solutions can be put in place to detect potential signs of intrusion.
While PRTG cannot be used as a substitute for an intrusion detection system, it comes with many functions that help to protect against cyberattacks:
In PRTG, “sensors” are the basic monitoring elements. One sensor usually monitors one measured value in your network, for example the traffic of a switch port, the CPU load of a server, or the free space on a disk drive. On average, you need about 5-10 sensors per device or one sensor per switch port.
Paessler conducted trials in over 600 IT departments worldwide to tune its network monitoring software closer to the needs of sysadmins. The result of the survey: over 95% of the participants would recommend PRTG – or already have.
Paessler PRTG is used by companies of all sizes. Sysadmins love PRTG because it makes their job a whole lot easier.
Bandwidth, servers, virtual environments, websites, VoIP services – PRTG keeps an eye on your entire network.
Everyone has different monitoring needs. That’s why we let you try PRTG for free.