Custom alerts and data visualization let you quickly identify and prevent issues caused by personal devices.
With the rise of remote work, policies for BYOD – or Bring Your Own Device – are being widely adopted. But the use of personal devices in your network brings security risks. It’s clear that BYOD requires specific strategies, including employee education on strong passwords and two-factor authentication. Just don’t neglect BYOD monitoring as a cornerstone of a comprehensive strategy.
Paessler PRTG network monitoring software provides you with all the tools you need to monitor bandwidth usage using protocols like SNMP, flow, WMI, and more.
Display the data in dashboards, and get real-time notifications as soon as bottlenecks occur. What’s more: you’ll get a list of devices that generate the most bandwidth usage.
Employee-owned devices in your network mean the chances of security breaches are increased. Support your BYOD security policies and security measures by using PRTG.
Monitor for signs of malicious activity or unauthorized access, such as data traffic spikes and abnormal access requests. If it detects unusual patterns, PRTG sends you immediate alerts.
MDM (Mobile device management) systems, NAC (network access control) solutions, IDPS (intrusion detection and prevention systems), SIEM (security information and event systems)…
All of these form part of a robust BYOD management strategy. And PRTG can monitor them to ensure they are up and running as they should be.
PRTG provides you with historical bandwidth usage in your corporate network over time, which helps you identify specific patterns. These include peak usage times or the maximum number of concurrent devices connected at any one time.
Use this data to optimize your network and plan for bandwidth usage of personal devices in your network.
Diagnose network issues by continuously tracking bandwidth usage of personal devices. Show data traffic volumes, device security, and other key metrics in real time. Visualize monitoring data in clear graphs and dashboards to identify problems more easily. Gain the overview you need to troubleshoot BYOD bandwidth and security issues.
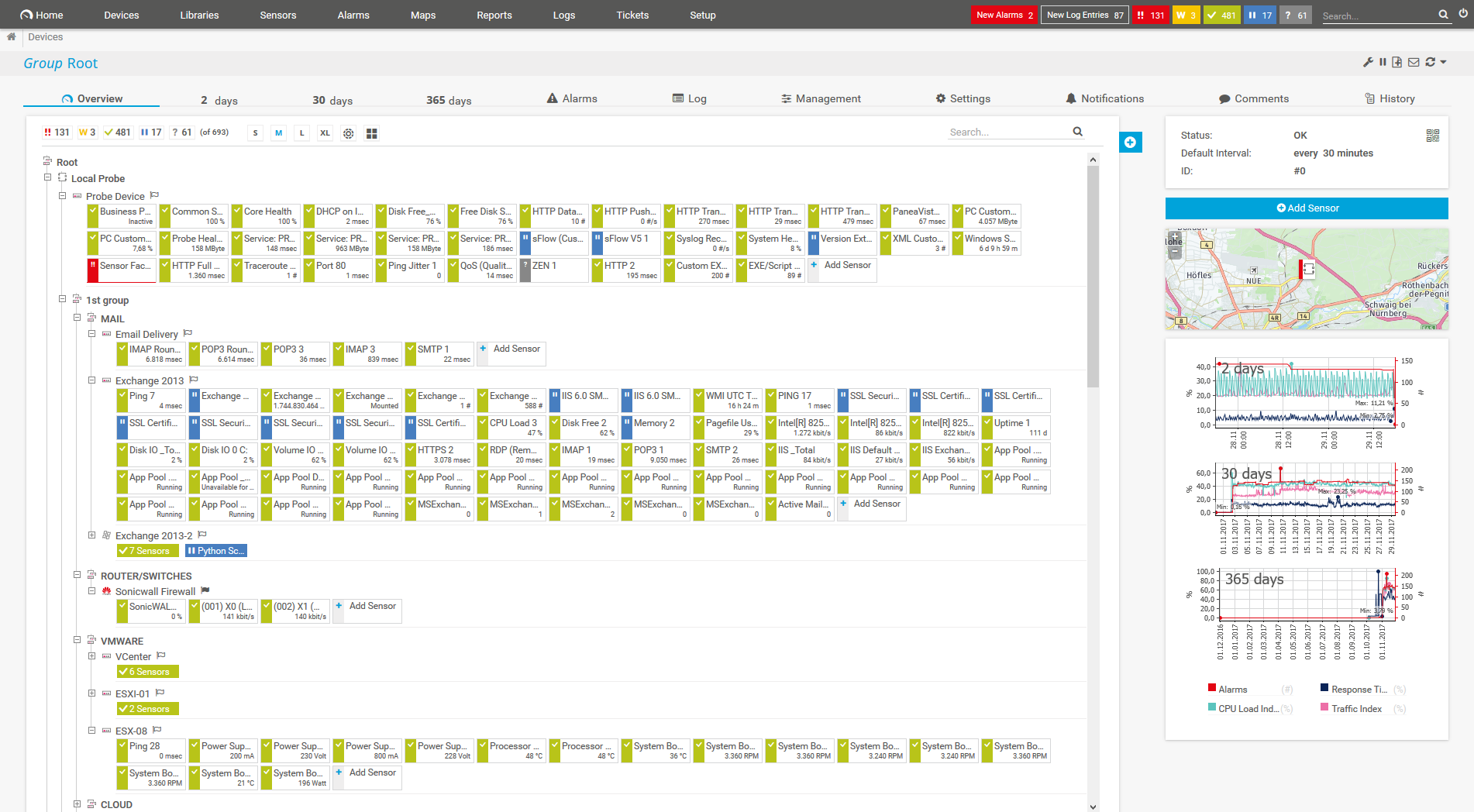
Device tree view of the complete monitoring setup
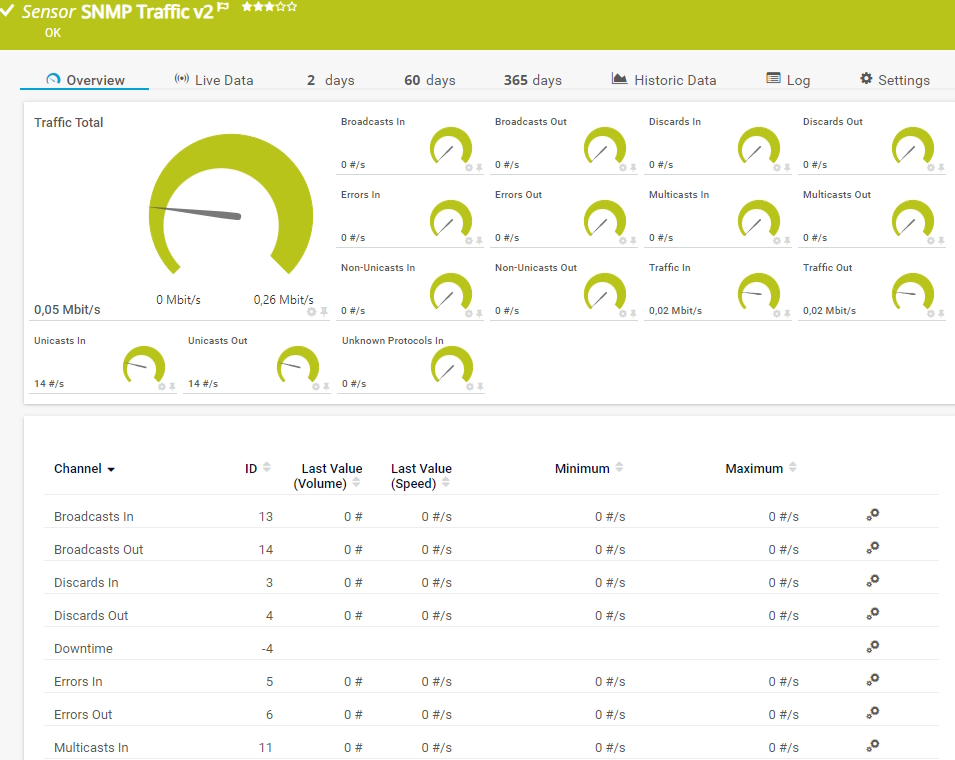
Preconfigured SNMP Traffic sensor in PRTG

Custom PRTG dashboard for keeping an eye on the entire IT infrastructure
See how the bandwidth usage of BYOD devices compares with that of other devices in your network, and get a feel of the overall company data traffic trends.
Decide how you need to see BYOD data, and configure custom reports with everything your team needs for BYOD management.
PRTG does it all: bandwidth management, uptime monitoring, server monitoring, data center monitoring, and much, much more. And it has fully featured alerts and notifications.
PRTG comes with more than 250 native sensor types for monitoring your entire on-premises, cloud, and hybrid cloud environment out of the box. Check out some examples below!
See the PRTG Manual for a list of all available sensor types.
Custom alerts and data visualization let you quickly identify and prevent issues caused by personal devices.
PRTG is set up in a matter of minutes and can be used on a wide variety of mobile devices.
Partnering with innovative IT vendors, Paessler unleashes synergies to create
new and additional benefits for joined customers.
Monitor all major physical hazards in IT rooms and racks such as critical climate factors, fire or burglary.
Osirium’s experienced management team has an outstanding track record in cybersecurity and automation, establishing its headquarters near Reading, UK.
Rhebo and PRTG offer a comprehensive monitoring solution for IT and OT environments: from condition monitoring through to anomaly and threat detection.
Real-time notifications mean faster troubleshooting so that you can act before more serious issues occur.
Network Monitoring Software – Version 25.3.110.1313 (August 27, 2025)
Download for Windows and cloud-based version PRTG Hosted Monitor available
English, German, Spanish, French, Portuguese, Dutch, Russian, Japanese, and Simplified Chinese
Network devices, bandwidth, servers, applications, virtual environments, remote systems, IoT, and more
Choose the PRTG Network Monitor subscription that's best for you
BYOD, or Bring Your Own Device, is a policy that allows employees to access the company network and corporate data using their personal devices – such as smartphones, tablets, laptops, and more – for work purposes. With the rise of remote work, the BYOD trend is now more prevalent than ever before.
Good BYOD management consists of several systems and solutions, such as mobile device management, cybersecurity and antivirus software, and network monitoring. It also involves extensive employee education.
There are many possibilities to measure bandwidth usage. Utilize the SNMP protocol, which is supported by many manufacturers. Analyze flow protocols. Monitor Windows devices with WMI. There are many options, and the best approach is to implement network monitoring software like Paessler PRTG that gives you as many possibilities to monitor bandwidth as possible, all in one solution.
No! PRTG monitors personal devices in the same way it monitors any device type: by analyzing how the device is connected to the network (for example, over wi-fi), how much data traffic it is sending and receiving, and so on. PRTG cannot access personal data on the device itself.
In PRTG, “sensors” are the basic monitoring elements. One sensor usually monitors one measured value in your network, for example the traffic of a switch port, the CPU load of a server, or the free space on a disk drive. On average, you need about 5-10 sensors per device or one sensor per switch port.
Paessler conducted trials in over 600 IT departments worldwide to tune its network monitoring software closer to the needs of sysadmins. The result of the survey: over 95% of the participants would recommend PRTG – or already have.
Paessler PRTG is used by companies of all sizes. Sysadmins love PRTG because it makes their job a whole lot easier.
Bandwidth, servers, virtual environments, websites, VoIP services – PRTG keeps an eye on your entire network.
Everyone has different monitoring needs. That’s why we let you try PRTG for free.